October 2022, Vol. 249, No. 10
Features
Harnessing Tacit Knowledge to Secure Operations Against Cyber-Threats
By Danielle Jablanski, OT Cybersecurity Strategist, Nozomi Networks
(P&GJ) — Across the energy sector and critical infrastructure in general there are many assets and systems deemed “crown jewel assets” or “mission-critical systems.” Depending on who you ask, nearly every digital component they rely on is potentially at risk in some way.
This painstaking reality is impacting every organization and facility across the oil and gas industry, as owners and operators continue to try to do more with less across brownfield and greenfield initiatives, maintenance projects and technology deployments.
The evolution of operational technology (OT) and industrial control systems (ICS) in oil and gas operations began with on-premises connectivity between systems, often using ethernet, to connecting multiple sites and often remote locations, to the expansion of supervisory control and data acquisition (SCADA) architectures, and increasingly the adoption of cloud technologies. Security is often iteratively applied and incrementally scaled.
The challenges that face information technology (IT) systems are generally solved differently than the types of issues facing OT systems. Prescriptive recommendations for improved security often overlook the realities of OT asset ownership, operation, transfer and chain of custody.
Limited resources, lack of technical competency, talent and expertise gaps and siloed communications are notable hurdles to the adoption of more robust and resilient security capabilities.
If a pipeline operator with distributed operations is unfamiliar with their network activity, and a change occurs, how would they know if it is security-related or operations-related? Their tacit knowledge is all that is required to investigate any change or incident. The problem is knowing when and where to investigate an issue before it becomes unmanageable.
Internal vulnerabilities are not perfectly matched 1:1 with external threat actor capabilities. Mitigating certain internal vulnerabilities won’t curtail threat actor capabilities to target and exploit your systems. Simultaneously, dedicating all of your resources to defending against a certain set of tactics, techniques and procedures (TTPs) may not significantly reduce risk across your organization.
OT cybersecurity solutions are evolving to centrally aggregate and apply machine learning to network behaviors – to understand what to investigate, when and why – with enriched data based on tacit knowledge of vendor control systems, context of processes and operations in a given environment, and the everchanging threat landscape.
Known Trends
Cybersecurity is top of mind given the flood of products on the market for clean and renewable energy, greenfield investments, and analytics promising increased efficiency and productivity. The industry 4.0 push for optimizing operations, enhanced resource allocation and efficiency, and maximizing production has led to the development of internet of things (IoT) use cases, predictive maintenance and digital twin solutions.
Survey data over the last decade summarize the following major trends:
- Adoption of new technologies continue to outpace cybersecurity and risk mitigation concerns, lacking documentation and data for security monitoring and network visibility.
- Industrial targets are seen as increasingly lucrative, unprepared targets that tolerate little to no downtime as threat actors continue to probe industrial networks.
- Organizations realize they are often ill equipped to deliver holistic cybersecurity for OT and ICS assets, devices and networks.
- Oil and gas companies are among the most likely to pay ransomware demands to retrieve data visibility and operational capacity.
Depending on the source and year of analysis, nearly half of industrial cyber-incidents go undetected. Owners and operators increasingly use and contract third-party equipment and technologies, creating a web of connected devices without visibility into the access levels and data traffic between them. Security concerns arise for data integrity and confidentiality concerns, loss of view or control of control systems, operational hazards and business disruption.
In addition, many oil and gas companies and industry organizations continue to identify insider threat scenarios as their top concern. Insider threat scenarios can be broken down into three categories:
- Compromised insider threat may be used as a conduit for exploiting vulnerabilities and exposures that go undetected.
- Malicious insider threat has intent to do harm or grant unauthorized changes and permissions to manipulate data, systems and processes.
- Negligent insider could be an employee or third-party change, implementation or update that results in error, failure, vulnerability or damage.
Industry-Specific Concerns
Asset owners may not know their OT or ICS are connected to the internet in some way, have no way to detect unauthorized changes, face mounting chain of custody and supply chain demands, and leave themselves at risk for remote takeover and control of assets. These risks may lead to manipulated products or processes, equipment damage or malfunction, unsafe conditions and/or unintended shut down of operations.
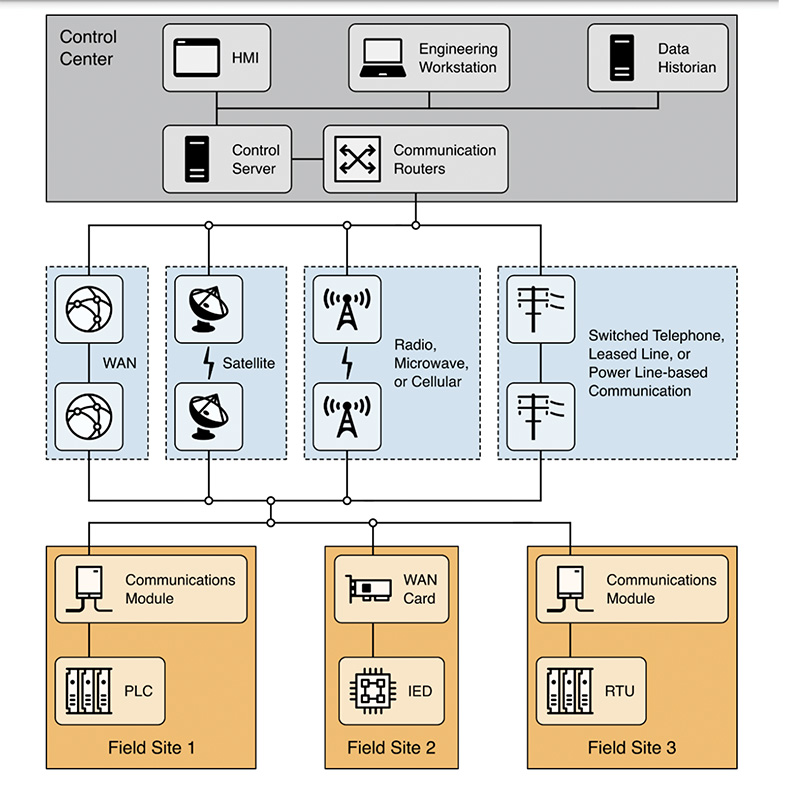
As an example, pipelines, pumping/compressor stations, remote production wells and other locations, often remote geographic locations, deploy some type of SCADA technology. Data from the equipment are transmitted to field-based programmable logic controllers (PLCs), which are typically ruggedized and built for the outdoors.
The PLCs communicate with gateways that transfer the data, via satellite, 3G cellular communication, and/or line-of-sight radios, to a gateway for a shared data center/server farm. Amazon Web Services (AWS), Microsoft Azure or the Google Cloud Platform provide more and more of these server farms.
Once transmitted to the server farm, data are evaluated by cloud-based analytics programs that use not just process data but other business information that can be applied to statistical models. Depending on the results of the analysis, the SCADA application feeds updated control logic to the PLC in the field. (Figure 1)
Despite the benefit of cost savings and outsourcing of SCADA expertise, owners and operators of SCADA systems may not consider the cybersecurity of their components, the integrity of OT and ICS data, operational impacts and best practices. Operators may not have any way of recognizing equipment failure for nodes attached to and communicating with the SCADA system.
The organization is in the dark in terms of detecting and monitoring new connections and tie-ins. Ultimately, they cannot diagnose performance issues, potential malware on the industrial network, or potential equipment failure or damage.
An unforeseen incident can cost millions in unplanned outages and maintenance. Visibility solutions for OT and ICS can help alleviate several pain points for operators needing to distinguish between malicious and benign behaviors and anomalies happening on their networks, with and between critical assets.
This capability is necessary for root cause analysis to determine whether an issue is caused by a cyber-threat, ransomware incident, equipment malfunction, misconfiguration or ghost drifting – when a device incrementally slips out of scope over time without oversight.
4 I’s of Visibility
In the days before built-in, automated and real-time visibility, operators would troubleshoot manually by reviewing point-in-time metrics of process data from meter and transmitter calibrations. They would look at the way the code was written in the flow computers, review data sent from the flow computers to the control system, to compare with the data historian, accounting software and other systems.
Today, vendor solutions incorporate intrusion detection for network security monitoring incorporating both network and process data, to passively scan for known vulnerabilities and indicators of compromise, investigate assets for deeper pattern analysis, due diligence and quality control. Custom alerts can be created based on the normal operations and parameters of systems operating in each end user environment.
Understanding and baselining both network and process data ensures visibility across:
- Inventory: automate understanding of digital components, devices and cyber-physical systems and infrastructure
- Integrity: of data at rest, in transit, in use and in view of operators for security and purpose-built operations
- Impact: proactive assessments of risks, malfunction and misconfiguration before an incident occurs
- Implementation: automate required mechanisms to capture data and communications once statically logged and reviewed
The Nozomi Approach
With an “assume breach mentality,” the focus for security products must be on reducing the severity of potential impacts, not on responding to worst-case scenarios only after they unfold. Instead of focusing resources on niche security programs, building intuition into security for purpose-built operations requires deep understanding of network and process data, customized rules and detections to prevent any type of cyber-incident – malicious or benign.
The more equipped we become at understanding network and process data and customizing detections based on the environment, the more capable our security solutions are to augment threat intelligence and overall security postures. Scalable customization results in superior situational awareness, where the impacts of cyber-scenarios can be limited by building in intuition and leveraging tacit knowledge. At Nozomi Networks, we have built an extensive library of communications patterns and process variables to inform end users’ customization.
We understand that OT/ICS cybersecurity is not a journey or a destination, but a constant relay race with partners and customers to stay ahead of the curve, continually creating new features for better situational awareness and actionable intelligence.
Author: Danielle Jablanski is an OT cybersecurity strategist at Nozomi Networks, responsible for researching global cybersecurity topics and promoting OT and ICS cybersecurity awareness throughout the industry. She serves as a staff and advisory board member of the nonprofit. Jablanski is a member of the International Society of Automation Global Cybersecurity Alliance (ISAGCA).





Comments