June 2017, Vol. 244, No. 6
Features
Multi-Mechanism Approach to Modeling Corrosion Threats to Pipelines

An innovative, common-sense strategy has been established to show the integrity hazard of pipelines attributed to internal corrosion deterioration mechanisms. The methodology provides guidelines for scheduling mitigation actions to prevent new corrosion, bringing any pre-existing corrosion damage to a standstill.
The threat-assessment method comes from basic, data-heavy approaches as it adopts use of “big-data” predictive analytical algorithms to classify pipelines according to established threats.
Pipeline failures attributed to internal corrosion occur with increasing frequency each year throughout North America in both the upstream (oil and gas production) and the downstream (natural gas and liquids transportation) sectors. Despite the recognition that pipelines are crucial to business and social well-being, the reality of high-consequence accidents in recent years has presented industry with unparalleled challenges:
- Unprecedented public interest in all pipeline activity.
- Unremitting pressure on industry’s social license to operate.
In response to the challenging business environment, there is a mandate for pipeline owners to develop better methods for threat assessment, to implement improved failure-prevention programs and to show stakeholders that these initiatives are working.
Of utmost concern to pipeline companies, regulatory agencies and the public are the circumstances causing internal corrosion failures within high-pressure pipelines transporting products to the pipeline. The likelihood of an internal corrosion failure for pipelines transporting non-corrosive fluids (by design) is nil, however, the probability of a failure on many of these pipelines may not necessarily be zero.
There is a substantial opportunity to optimize the cost of operating and maintenance activities while delivering improvements to pipeline performance, regulatory compliance and profitability by addressing root-cause factors affecting pipeline performance.
The primary aim of root-cause analysis:
- Identify the factors that led to the magnitude, the location and the timing of the harmful consequences of a past events.
- Determine what behaviors, actions, inactions or conditions need to be changed to prevent recurrence.
The reason to identify all solutions to a problem is to prevent recurrence at lowest cost and in the simplest way. If there are alternatives that are equally effective, then the simplest or least expensive is preferred.
When applied to a formal pipeline integrity management (PIM) program, a root-cause approach demands that four compulsory key performance indicators (KPI’s) be addressed:
- Pin-point critical pipelines, otherwise being over-looked, according the extent of pre-existing corrosion damage caused by historical operations – know the historical threats and present condition of each pipeline and avoid missing critical pipelines that eventually will suffer a leak.
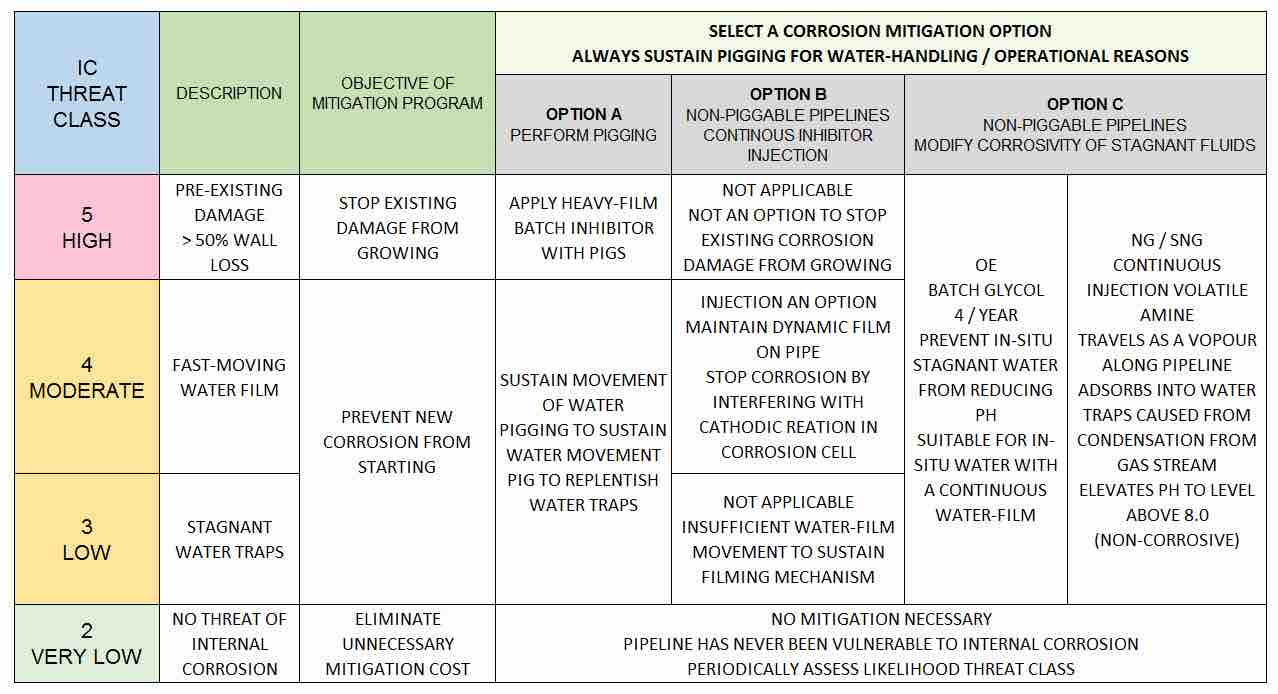
- Perform proper maintenance on all critical pipelines appropriate to render pre-existing corrosion damage inactive – do the right thing to stop existing corrosion from growing into a leak event.
- Trigger an alert when a new critical risk arises, and adjust threat mitigation to stop new corrosion from starting.
- Directly inspect pipeline condition for to establish extent of actual corrosion damage – find severe corrosion damage and repair it prior to a leak event.
Application
Step 1 – Classify pipelines according to over-life threat and present condition
A PIM program is composed of the policies, practices and procedures implemented by the owner/operator to ensure the long-term safe and efficient operation of pipeline assets.
Implementation of such a program allows operators to practice safe and environmentally friendly operating and maintenance. A key component of an effective PIM is a reliability threat assessment methodology:
- Pin-point critical pipelines that are otherwise being overlooked according the extent of pre-existing corrosion damage caused by historical operations.
- Know the historical threats and present condition of each pipeline.
- Avoid missing critical pipelines that eventually will suffer a leaks.
Big data within a PIM program refers to predictive analytics, user behavior analytics or certain other advanced data analytics methods. Predictive data analytics requires intelligent use of easily available data to discover new correlations and spot trends to classify pipelines. This is based on threat failure and creation of an action plan to prevent future leaks.

When scrutinized data patterns within North America pipeline data sources, it is confirmed pipeline accidents repeat themselves in patterns that are significantly different than those characteristics of non-failed pipelines.
By taking advantage of the markedly diverse data patterns, it remains a straightforward task to pinpoint critical pipelines expected to have pre-existing corrosion damage (at peril of leaking), and similarly to classify non-critical pipelines that at no time have been exposed to a corrosive condition, which are candidates for reducing management cost.
Data patterns derived from predictive data analytical methods are applied to a corporate pipeline inventory to establish if the likelihood for each of the three mandatory contributing factors align to suggest pre-existing damage, or an absence of contributing factors.

Step 2 – Establishing the extent of pre-existing damage
The benefit of this method is it creates an accurate profile of potential corrosion threats along the pipeline by application of sophistocated fluid modeling techniques.
The corrosion threat profile is most often different than the a profile created by existing industry-standard methods; it is much more realistic as it considers historical mitigation measures, and the associated benefits of avoiding the formation of corrosive regions along the pipeline length.
The method pin-points isolated locations where the most severe corrosion may occur if corrosive fluids are delivered into the pipeline; oferring the owner the opportunity to narrow-the-focus towards those pipelines most likely to trigger a catastrophic accident.
Step 3 – Create mitigation guidelines for field, operations
A formal PIM program places structure around existing routine activities and aligns mitigation actions with the actual corrosion threats:
- Perform proper maintenance on all critical pipelines appropriate to render pre-existing corrosion damage to be inactive
- do the right thing to stop existing corrosion from growing into a leak event – stop spending money on non-vulnerable pipelines
Throughout the implementation of a PIM strategy, the activities carried-out in the field on a day-to-day basis are the same as present practices. However, they are better focused because of an enhanced understanding of the hazard profiles throughout the pipeline network.
For more than 65% (typical of oil and gas gathering systems) of operating pipelines, no mitigation action is necessary as all three elements necessary to support corrosion initiation and growth do not (and have not) existing within most pipelines.
Additionally, for gas and liquid transportation pipelines, less than 2% of all structures are typically identified as at-threat of internal corrosion.
Application of Analytics
A broadly-held paradigm suggests all pipelines transporting corrosive fluids are likely candidates for a leak, and that money must be spent carte blanche to address a common threat.
A surprising outcome of predictive data analytics reveals pipeline leaks are highly unlikely to occur (statistically rare events) bearing in mind the extent by which pipelines are exposed to corrosive fluids, and this aligns well with industry experience:
- Less than 2% of all pipeline operations exposed to corrosive fluid service throughout North America over the past 25-years have failed because internal corrosion.
- An extremely low result contradictory to the idea that pipeline leaks are just about a certainty unless the threat is stopped by application of mitigation.
Unfavorable pipeline performance is often caused by unexpectedly corrosive fluids being delivered into the pipeline as opposed to steady-state exposure to ordinary production fluids; true for all pipeline classes.
Patterns observed as an outcome of looking at regulatory, public and operating company data sources show over 80% of internal corrosion damage (and failures) are attributed to accelerated corrosion attack associated with unexpectedly corrosive fluids, as opposed to corrosion associated with steady-state pipeline operations.
Contributors to this outcome:
- Up-lift of non-routine, unexpectedly corrosive fluids at start-up of upstream wells after a shut-in period or the introduction of especially corrosive fluids from upstream processing facilities.
- Creation of iron sulphide (black powder) corrosion product within pipelines, which is not normally transporting corrosive fluids suggests the presence of an additional corrosive agent.
- Pipeline failures somethimes occur on pipelines examined with in-line inspection tools showing no corrosion damage.
- Rapid time-to-failure confirms highly-corrosive material presents an unexpected corrosion damage at a rate much higher than possible from steady-state fluid production.
Conclusion
There is a substantial opportunity to reduce the money spent on corrosion prevention while delivering improved pipeline performance – typically 65% less spent on corrosion mitigation.
The process described relies upon application of historical performance patterns to classify operating pipelines according to potential exposure to internal corrosion and to make certain mitigation and inspection decisions are appropriate.
The use of this common-sense application of predictive data analytics can stop pre-existing corrosion damage from continuing to grow and to prevent new corrosion from starting.





Comments