February 2016, Vol. 243, No. 2
Features
Does Aligning Cybersecurity, Process Safety Approaches Reduce Risk?

Cyber-attacks are more hostile and frequent than ever. We’ve all heard news stories about how intellectual property and private information have been stolen by hackers. When this happens, it can be costly in some cases and embarrassing in others. However, for industrial operations, the stakes are much higher. It is absolutely essential we protect industrial operations from cyber-interference to avoid any compromise to the safety and security of the plant, its people and the environment.
A recent news story published on Bloomberg.com described a 2008 explosion at an oil pipeline, identifying a cyber-attack as the initiating cause. According to the article, “Hackers had shut down alarms, cut off communications and super-pressurized the crude oil in the line. The main weapon at valve station 30 on Aug. 5, 2008, was a keyboard.”
Too many similar stories have appeared in the news since, and the bottom line is this: increasing dependence on digital networks and integrated systems in industrial plants can increase the potential for hackers to do a lot more than just steal documents if the correct cybersecurity strategy has not been put into place.
Cyber-threats have increased tremendously for every industrial operation. In today’s world, protection against cyber-attacks is essential if modern networked control systems are to perform securely.
 The increased prevalence of industrial networks means that cybersecurity is now more closely linked to the safe operation of industrial operations and their processes. A solid cybersecurity protection plan must therefore be an integral part of any modern plant’s operating strategy. The similarities in protection approach between process safety and cybersecurity warrant an objective and detailed look at how they are similar and how they differ. The comparison should be made not only from a procedural point of view, but also from an organizational perspective.
The increased prevalence of industrial networks means that cybersecurity is now more closely linked to the safe operation of industrial operations and their processes. A solid cybersecurity protection plan must therefore be an integral part of any modern plant’s operating strategy. The similarities in protection approach between process safety and cybersecurity warrant an objective and detailed look at how they are similar and how they differ. The comparison should be made not only from a procedural point of view, but also from an organizational perspective.
Questions Every Plant Owner Must Answer
From the boardroom down, every plant owner must be able to answer with confidence three critical questions:
Do we understand what could go wrong?
Do we know what our systems are to prevent this from happening?
Do we have the information to assure us they are working properly?
These questions should be answered continuously during the lifecycle of a plant, not only during the design or planning phase of the facility. Control systems are designed, built and tested before they are operated in the plant and are maintained according to the adopted lifecycle program. And official standards exist for both the safety lifecycle (ISA84/ IEC61511 functional safety – safety instrumented systems for the process industry sector) and cybersecurity lifecycle (ISA/ IEC 62443 network and system security for industrial process measurement and control).
Looking at the three questions in the context of the relevant phase of the safety or cybersecurity “life cycle” will help companies understand what they should be doing and when. Today’s plant must execute a cohesive strategy for both safety and cybersecurity to ensure continuous operational integrity for the entire plant.
Safety and Cybersecurity – More Similar than Different
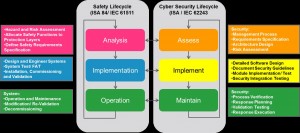
As shown in the figure below, plant owners can look toward established process safety standards for cybersecurity guidance. It shows distinct similarities between ISA84/IEC61511 and IEC62443 standards that apply to the safety and cybersecurity lifecycles, respectively.
Industrial operations typically follow an established lifecycle. Starting at the “analysis phase,” attention is given to identifying and understanding what can go wrong, what the likelihood and impact is, and then defining what protection is required to manage and mitigate the risks.
From the “implementation phase,” systems and equipment are developed and engineered, built, tested, verified and documented. Often there is a formal Factory Acceptance Test (FAT) or other type of customer verification before the equipment is shipped to the plant where it is then installed, commissioned and put into operation.
Once in the “operation phase” it then becomes the responsibility of the operators and/or engineers who will operate and maintain it for the rest of its life. It is worth noting at this point that the “operate/ maintain phase” of the lifecycle typically lasts much longer than any other phase of the project.
With good practice and rigor applied during the analysis/assess and implementation phases shown above, the answer to all three questions should always be a firm “Yes.” However, the biggest challenge comes when answering the three questions in the operations phase. Why?
The operation phase can last 10 years or more (typical assets operate from 30-plus years).
Changes may be made to the system during its lifetime. For example, when driven by market demands or changing manufacturing practices.
Risks and threats change – asset owners must continue to adapt and monitor both their safety and security measures to ensure that they stay on top of evolving risks and track any such changes.
Organizational Challenges
We’ve discussed prevailing standards and execution theory to align cybersecurity and process safety. And we’ve seen that frameworks exist to ensure that both are included in initial system design, verified during acceptance tests, properly commissioned and then maintained for the life of the plant.
Another challenge often faced when it comes to leveraging and coordinating process safety and cybersecurity is organizational in nature and often the result of historical practices in place. Traditionally, cybersecurity has had little to no impact on manufacturing processes as it affected only the computer systems in the plant, which were the domain of the IT department. Automation systems were the domain of the control and instrumentation department, sand safety the responsibility of the process safety group.
Until recently, there was no reason to coordinate or overlap the responsibilities of these groups. Today, however, we understand Industrial Automation Cybersecurity (IACS) and we have witnessed its direct impact on process safety. Cybersecurity, once solely the concern of the IT department, now impacts process safety and the plant organizations responsible for it.
In order for coordinated approaches between the various disciplines as discussed earlier to be effectively put into practice, it is imperative to bridge any organizational gaps between Information technology (IT) and Operational Technology (OT), and design an organizational framework where all groups can continuously collaborate across all phases of a project’s lifecycle – from the initial design into the build and operational phases.
The groups can then work together to ensure cybersecurity is designed into systems, verified with process safety measures during FAT and revalidated following any process changes in the plant, just as safety systems are today. When selecting a consultant to work with you to provide safety lifecycle services, it is a good idea to select one who also has cybersecurity expertise. Such a supplier will be an invaluable resource to help you coordinate your approach to safety and security.
Today’s reality means that we must support and drive close organizational alignment and/or effective collaboration between the teams or groups that traditionally have little history and experience of working together. Companies must find ways to foster continuous, effective working relationships between IT and OT if operational integrity is to be achieved. Looking to the historical journey of process safety implementation in the industry for guidance can help begin to address these organizational challenges, often one of the most difficult tasks companies face today as they increasingly embrace modern, networked systems.
Process automation and control technologies continue to evolve rapidly. The linkage between manufacturing assets possible today has been described as the “next industrial revolution.”
This new era will offer enterprises the possibility for significant improvements in safety, efficiency, product quality and profitability, but if not implemented with cybersecurity in mind, can also lead to increased threats of cyber-attacks, which must be addressed if plants are to maintain operational integrity.
The disciplines of safety and cybersecurity are truly more similar than different. Effective coordination of the two sets of lifecycle activities will result in a “stronger together” approach to IACS AND process safety. The newer discipline of IACS can leverage many best practices from the more established disciplines of process and functional safety.
Effectively coordinating these areas and ensuring plant safety and cybersecurity teams are working closely together will allow companies to take advantage of the latest technological developments in a way that is safe secure and protects their operational integrity.
 Author: John Boville is the Process Automation services marketing manager for Schneider Electric. He has been with the company for more than 20 years and in engineering, management and marketing roles for industrial automation solutions for over 30 years. He is based in Michigan and can be reached at john.boville@schneider-electric.com.
Author: John Boville is the Process Automation services marketing manager for Schneider Electric. He has been with the company for more than 20 years and in engineering, management and marketing roles for industrial automation solutions for over 30 years. He is based in Michigan and can be reached at john.boville@schneider-electric.com.





Comments