August 2018, Vol. 245, No. 8
Features
Securing Open SCADA Systems for Pipeline Operations
By Chris Harlow, Bedrock Automation
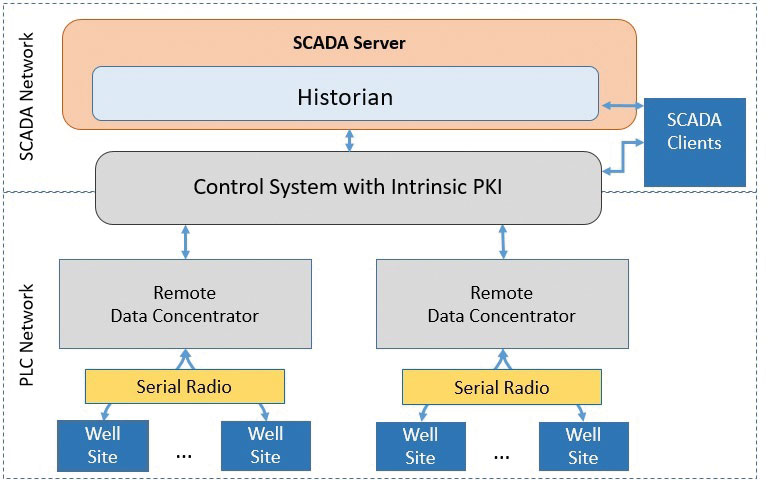
Traditional SCADA systems on which many pipeline operators rely for operational control are vulnerable in at least three main areas: the operational information on which they rely to supervise control and access the plant data; the production data that emerges in the wake of pipeline operations; and the control logic that opens and closes valves, starts pumps, and otherwise manages field devices. The more open the flow of this of data, the more cost-effectively the plant can be run, so there is much to be gained by securing the data exchange.
One significant step in securing open communications is the advancement of OPC UA (open platform communications unified architecture). This provides a standard for managing open communications across multivendor applications and devices. Its latest rendition includes protocols by which users can authenticate and encrypt communications, so that each device or workstation participating in the network has maximum certainty that communications are protected and authentic.
The OPC UA Connection
OPC UA is becoming the communication standard of choice for SCADA communications because it is simple and scalable, as well as more secure than other communications protocols. When used with a secure control system, the control system would have an embedded OPC UA server. The OPC UA client software can easily discover any controller on the network that is running an OPC UA server and connect instantly to view the data. It would instantly know what data is available and whether the requestors have rights to access it.
Once the OPC UA clients find a device running an OPC UA server, it scales easily to allow multiple clients to connect and exchange data securely among servers and clients. That data can then be used in applications that run on PLCs or other controllers, drawing on industry standard application software and engineering tools, which can be used to construct powerful, complex programs using reusable programming objects.
Object-oriented programming has been semi-available in ICS programming for many years but the methodology has matured considerably, making it much easier to develop programs that are easy to build, troubleshoot, and scale by building on previous tested objects. If you have a pump station running three different motors, and then suddenly you need to bring a pump station online that has four motors, for example, you wouldn’t have to develop new code from scratch, you could just extend the three-motor version by dragging and dropping an already programmed motor block.
Contributing also to the scalability are options for defining the rules that govern data communications. You can control the behavior of the data, allowing it to be read-only, write-only, or read-write; and set triggers for data movement, e.g. whether it is transmitted on change or continuously updated.
Securing Communications
Such attributes are what makes OPC UA communications desirable for building efficient automation applications, but it is a third quality, the ability to help users manage authentication, that makes it also securable. When the DHS uses the term managing authentication, they refer to preventing adversaries from gaining control of legitimate credentials, especially those associated with highly privileged accounts.
Compromising these credentials allows adversaries to masquerade as legitimate users. The ability to manage trusted information and access control is what make OPC UA more secure than other industrial communication protocols. It allows for at least two levels of cybersecurity protection.
In the default level, OPC UA enables the application developer to sign the certificate that contains the key that decrypts encrypted data. Suppose you built an online database and wanted to protect the data. You might encrypt it and assign a password, which would enforce a basic level of trust that whatever or whoever is trying to access the information and controls is properly authorized to do so. Security is limited, however, by the fact that anyone who knows the password is granted entry to the data.
The second approach also draws on the capability of OPC UA to facilitate cyber security, but takes it further by authenticating all communications according to encryption and decryption keys that are buried deeply and securely into the electronics of the control system and authenticated against a third-party root of trust. That way, anyone who obtained the password or access key, must also pass muster of a third-party certification authority, which verifies the password against some other secret information it knows, but an unauthorized intruder would not know.
Now, imagine that additional point of verification deployed, not just at one point of entry but thousands of times at light speed and at numerous gateways within and between system components, in a complex infrastructure of encryption and decryption keys that would take even the most powerful computers decades to crack. The technology for managing this is called a public/private key infrastructure (PKI) and embedding a PKI and an OPC UA server into an industrial control system enables a secure exchange of information between control systems, SCADA applications and industrial devices.
Pinnacle Midstream, a Houston-based supplier of storage and processing services for the oil and gas industry, has implemented a control system with embedded cyber security as the automation platform for its crude oil receipt and delivery points. The Bedrock system from Bedrock Automation, will coordinate flow of product from partners, through the Pinnacle processing facilities and onto refiners and shippers.
Toward a safe, open future
Intrinsic PKI provides OPC UA a secure conduit to enforce application whitelisting and secure remote access. Control system vendor Bedrock Automation, for example, also reduces attack surface area by replacing traditional backplane pins with an electromagnetic backplane and that same vendor has announced embedded monitoring and response functionality.
Pipeline application developers who are now planning to take full advantages of the cost and operational improvement benefits of open SCADA would do well to seek out control technology with embedded cyber security. It could significantly reduce the chances of a cyber-attack going forward, and should ideally come free with the cost of the control system. P&GJ

Chris Harlow, senior product manager, Bedrock Automation has extensive process control and industrial control system experience. He is currently working to develop and implement an innovative control system architecture that is based on open and interoperable standards, but is also secure from cyber-attacks. Before joining Bedrock Automation, Chris developed control systems for a variety of industries including oil and gas both upstream and downstream, robotics, cryogenics, food and beverage, and commercial applications.





Comments