February 2013, Vol. 240 No. 2
Features
Latest Threats To Pipeline, Production And Process Management Systems

(Editor’s Note: The original “Hacking the Industrial SCADA Network” (Part I) aritcle was first published by Pipeline & Gas Journal in November 2009. This article, Part II, is the summary of what has happened since the original publication, and the outcome of predictions which first appeared in Part I. See full copies of the actual whitepapers for complete details.)
The Secret War: Stuxnet, Duqu And Flame
The highly complex computer worm called Stuxnet, targeted at sophisticated industrial control systems, was first identified in July 2010. The arrival of Stuxnet changed everything…as it was a harbinger of the shape of things to come.
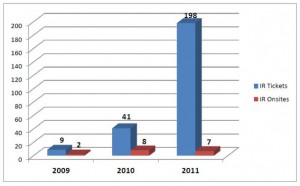
Summary of Critical Infrastructure Incident Reports to ICS-CERT, 2012
Stuxnet sparked international press coverage and exposed to the business community the digital face of cyber espionage, cyber warfare, sabotage and electronic diplomatic sanctions. For industry leaders, it raised the specter of international industrial competition fueled by the theft of proprietary trade secrets, intellectual property, business, government and military secrets, and the potential loss of all the advantages of an advanced technological society.
Stuxnet targeted SCADA (Supervisory Control and Data Acquisition) systems. SCADA and other legacy control systems have been used for decades in power plants and distribution grids, oil and gas refineries, air traffic and railroad management, pipeline pumping stations, pharmaceutical production, chemical plants, industrial processes, automotive assembly lines, automated food and beverage lines, water treatment plants, major dams, and many other forms of automation and production.
Stuxnet was likely released a full year before its discovery. It was designed to replicate itself while searching for very specific industrial software applications that run behind Microsoft Windows® operating systems. Stuxnet was followed in 2012 by the discovery of two closely related forms of malware, the Duqu worm and Flame. Duqu searches for information that could be useful in attacking industrial control networks and smuggles password information back to its command and control center. Flame existed several years before being discovered, and can also record Bluetooth communications.
A Clear And Present Danger
The worms Stuxnet, Duqu and Flame have been captured, quarantined, dissected and studied in captivity. The worm segments have been analyzed and published in reports, whitepapers, blogs, chats and bulletin boards. Unfortunately, the result of all the published scrutiny is that the building blocks of Stuxnet exploit code are out there and available to be used to potentially harm the rest of us. A knowledgeable hacker can use those bits and pieces like modular building blocks to create newer, better malware.
The hacking incidents listed in “Hacking the Industrial Network” (Part I) spanned 12 years and contained 29 publically reported incidents. The hacking incidents specifically listed here in Part II (please visit wwwe.pgjonline.com for entire list) span only four years and contains more than over 55 notably disturbing incidents affecting thousands of companies. The pandemic rate of infection is accelerating.
Why The Petrochemical Industry Is Vulnerable
Some may still believe that their SCADA networks are not susceptible to eavesdropping, hacking or virus propagation because industrial SCADA systems are difficult for an outsider to understand – or that their networks are “air-gapped” to separate them from the Internet. It is not true. Access to the Programmable Logic Controllers (PLCs) used throughout your industrial network, including critical U.S. pipeline and refining infrastructure, is possible from indeterminate remote locations outside the country, without ever visiting your site, through multiple routes into the heart of your network.
- March 2009 — An IT contractor is charged and later pleads guilty to disabling the leak detection system alarms of three offshore oil rigs operated by Long Beach-based Pacific Energy Resources. Several articles in 2009 discuss the vulnerability of offshore rigs to hacking as a result of the “integrated operations model”, and Popular Mechanics published a piece explaining: “How Hackers Could Take Down a Natural Gas Pipeline”.
- During 2009 — Hackers hit oil and gas firms. The intrusions are multi-staged, multi-vector, pervasive and sustained. Two years later, in February 2011, anti-virus development company McAfee publishes a whitepaper naming the operation as “Night Dragon” because it appears to originate from China. The persistent attacks target global oil, gas and petrochemical companies, utilizing RATs (Remote Access Tools) to exfiltrate propriety operation information, legal contracts and sensitive financial information regarding oil and gas field auctions and bids. The perpetrators also collect configuration data from SCADA systems.
- August 2009 — Azerbaijani News reports that hackers with alleged Russian IP addresses attacked servers controlling the energy pipeline from Azerbaijan to Europe (bypassing Russia) causing suspension of BTC (Baku-Tbilisi-Ceylon) operations and forcing the company to redirect the oil through the Russian Baku-Novorossiysk pipeline.
- During 2010 — Following the dramatic source-code stealing attacks designated by Google as “Operation Aurora”, a released cache of pilfered emails written by analysts at the security firm HBGary reveals similar attacks had also hit ExxonMobil, Royal Dutch Shell, BP, ConocoPhillips, Marathon Oil and DuPont, some as much as two years earlier. The secret theft of bid data revealing the quantity, value and locations of oil discoveries worldwide is one of the objectives.
- August 2011 — A McAfee whitepaper exposes “Operation Shady RAT”, a five-year targeted operation that includes attacks on natural gas distribution, as well as federal, state and county government, defense and construction. Most of the intrusions were occurring in the United States and continued for months and years without discovery. The whitepaper’s author, McAfee’s Vice President of Threat Research, Dmitri Alperovitch, writes that he now divides Fortune 2000 companies into only two categories; those who know they have been compromised, and those who are blissfully unaware they have already been compromised.
- July-September 2011 — More than 29 chemical and defense firms are targeted using the “Poison Ivy” Trojan, dubbed by a Symantec whitepaper as the ”Nitro Attacks” in October 2011. The attacks managed to gain “root” (Administrator) access, primarily to identify and steal intellectual property.
- Also in October 2011 — The U.S. Department of Homeland Security issues a bulletin warning of ongoing gas, oil, chemical, water and sewage hacks.
- November 2011 — Hackers attack Norway’s oil, gas and defense businesses. Access is obtained through carefully crafted, targeted emails that appear to come from legitimate sources, but contain a virus which does not trigger anti-malware defenses. Norway’s National Security Agency (NSM) states that industrial drawings, contracts and current negotiation documents were extracted, a loss of closely held secrets and intellectual property to cyber thieves.
- April 2012 — The Department of Homeland Security announces that attacks on oil and natural gas organizations began five months earlier in December 2011. They report that the 200,000 mile U.S. natural gas pipeline network has been under a persistent intrusion campaign that begins with tightly focused “spear-phishing” email attacks.
- August 2012 — An attack hits Saudi Aramco oil operations. The “Shamoon” virus wipes clean the hard drives of 30,000 Saudi computers. Five days later, a similar attack takes place at Qatar’s RasGas. It has been speculated that many other energy organizations may have also been affected as a result of authorized network access through joint venture partnerships.
- October 2012 — Unknown attackers target the communications of Iranian offshore oil and gas platforms.

Industry Recommendations
The existing SCADA vulnerabilities and some precautionary measures are well described in whitepapers by Idaho and Lawrence Livermore National Labs. A simple solution involves implementing layers of defense referred to as “defense in depth.” Network segmentation, departmental firewalls, anti-virus and intrusion detection methodologies protect departments and systems.
Leading commercial antivirus software can work fairly well to create layers of protection in the front office of an organization, an area not adversely affected by the continuous updating of virus signatures needed to keep up with new virus variants created every few seconds. Some IT routers and switches can also provide Virtual Private Network (VPN) protection when installed in clean, air-conditioned rooms within production areas.

In harsh environments, however, with heat, dirt, moisture and vibration, standard telecommunications equipment fails rapidly. And at the lower echelons of production, the very basic PLCs and legacy industrial controls do not have the chip sets and processing capability to authenticate commands or identify malware. In a 24/7 production environment, it is risky to allow third-party software to constantly introduce updates that have not been vetted in isolation before being implemented, as these may produce other unintended consequences.
As identified in “Hacking the Industrial Network” (Part I), four years ago there were listed a handful of companies offering potential solutions applicable to the factory floor. Most of these have not updated their products or advanced technically and have not succeeded in significant market penetration.
I consider only two of the listed products to be the most viable as they offer the kind of security features that would be required. These are the Innnominate mGuard system, now also available from Phoenix Contact and the Tofino device, now available from Hirschmann. The mGuard industrial module was able to detect, divert and alert administrators to illicit “zero-day” probes by Stuxnet malware, as shown in independent laboratory tests at an IT University. Unlike anti-virus software, it could do so without any prior knowledge of Stuxnet’s existence, capabilities or viral signature.
Let’s run down the checklist of desired security features quickly. The following table contains a summary. Other technical reasons for selecting security equipment for industrial applications are explained in greater detail in Part I.

List of Required Industrial Network Security Equipment Capabilities
SCADA Security Outlook
State-sponsored theft of proprietary trade secrets, intellectual property, business, economic, government and military secrets, and all the advantages of a technological society are already being siphoned away at an alarming rate, with the losses measured in billions of dollars as we hemorrhage away the advanced products of our intellect. Hacking is the current province of criminal organizations, nation states, foreign competitors, and potential cyber terrorists.
There is no reason for this lack of implementation of industrial network security other than inertia. The security technology already exists, and simple, economical solutions are readily available and easily implemented. The risks are clear, and the activity is escalating. We can either act now to prepare for the next wave, or delay and procrastinate, and be perpetually behind the curve when the next bad thing occurs…and those other procrastinators are “overtaken by events” for which there is no time to respond.
A detailed study of specific recommendations and technical solutions is contained in the full white paper “Hacking the Industrial Network” (Part I) and the full version of this white paper (Part II). Complete copies, including footnotes, clickable Internet links and detailed research references can be downloaded from the International Society of Automation (www.ISA.org) and from www.innominate.com.
Author
Frank Dickman, BSMAE, RCDD, is a widely experienced engineering consultant and former delegate to NEMA, TIA/EIA, ISO, CENELEC and the BICSI Codes & Standards Committees. He is a technical consultant to a
number of leading data communications firms and is a recognized expert on U.S. and International physical infrastructure network standards. Beyond telecommunications, his experience includes consulting engineering work for petroleum refineries, chemical plants, conventional and nuclear power plants, auto manufacturers and the aerospace industry. He can be reached at frankdickman@yahoo.com.





Comments