February 2013, Vol. 240 No. 2
Features
Solving The Cybersecurity Puzzle
“Energy firms have spent vast sums on the security of their information systems, but they must reorient from a reactive, tactical posture regarding intrusions and attacks to a more strategic, holistic view that expands beyond the categorization of the issue as only an IT problem. For the energy industry, Cybersecurity is not just a technology problem (or puzzle) but rather is one that includes the larger dynamics (or bigger picture) of information and operations.” — Baker Institute, Cybersecurity Issues & Policy Options for US Energy Industry
An Oil & Gas/Pipeline Cybersecurity Puzzle – The Initial Step
If you ask a hundred people to define the initial step in solving a complex jigsaw puzzle, many will say it is to construct the puzzle’s borders and then fit the remaining pieces within the border. However, the initial step is to first look at The Picture on the box to gain an understanding of what you are trying to construct and then determine the best strategy to complete the puzzle.
Once we have an understanding of what we are trying to solve, we Build the Border, Group like Pieces into piles and Interlock the Pieces to form a completed puzzle. And with complex puzzles, we often Seek Expertise to help with strategy and/or work in finishing our task – how many times have you been staring (often for hours) at an incomplete puzzle and a friend walks by, picks up a piece and simply places it in the puzzle. We welcome the help but are a little frustrated that we did not see that specific solution. Finally, success is achieved when no pieces are left and the puzzle (our effort) and picture (our goal) match! Cybersecurity will always be a high-stakes puzzle – one that demands a defined goal, a smart strategy, the right technology and risk adjustments, and an unblinking eye on the adversaries’ expanding capabilities.
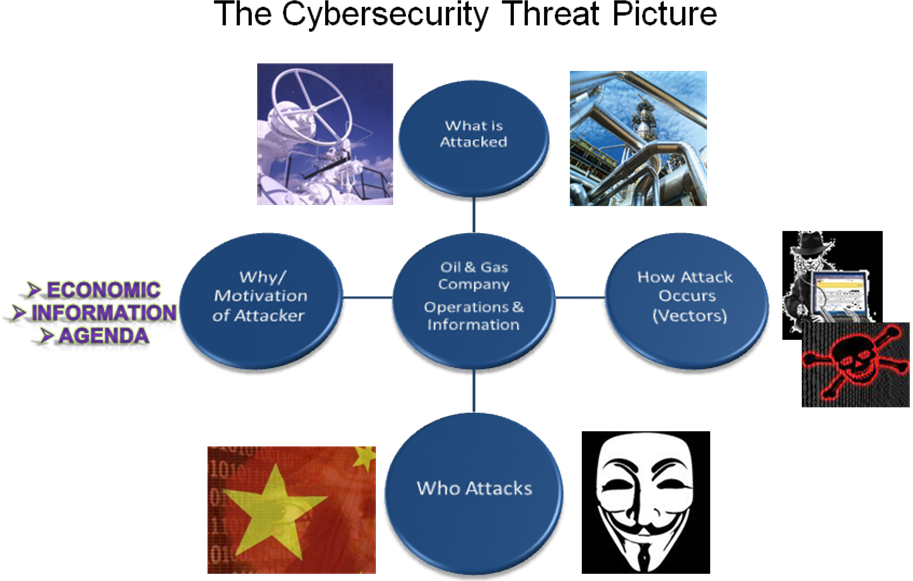
The Cybersecurity Threat Picture
Gaining a beneficial and clear understanding of the cyber threat can be somewhat daunting and may cause many oil and gas personnel to simply say, “Our IT guys handle this stuff”. As an adversary, that is exactly what I’d want – a limited number of company personnel who understand: what I am after, how I am resourced to succeed, my tactics to acquire it, why I am successful, and most importantly what a company can do to limit my success. And the adversary is not without assistance in helping keep cybersecurity complex and challenging (but not difficult) to comprehend. In performing background research for this article, I used Google to search for “Understanding the Cybersecurity Threat” and came up with 29,700,000 results! So let me offer some insight to help you better understand the threat picture so you do not have to spend hours going through all the websites. By the way, I wonder how many of those websites contain malicious viruses and were posted by a hacker? This is how individuals like me and your company’s cyber experts think – strange, but be glad we think this way!
Who Attacks & Their Motivation
Over the past couple of years, we have heard terms like Duqu, Night Dragon, Stuxnet, Shamoon and Flame, which are names of cyber attacks — some specifically targeting the energy sector. Many of these attacks were most likely the integration of cyber criminals who seek financial reward, with nation states who have deep resource pockets and expertise to deliver a successful return on their efforts – access, information theft, and the position to further disrupt, destroy or degrade operations.
As the box to the right calls out, there are four adversarial categories – each with specific motives – but it is the nation state that offers the greatest challenge to the energy sector. Why? Quite simply, the nation state brings together an industry’s operational expertise (how a refinery runs, what are its critical operations, etc.) with cyber criminals and hackers who understand the weaknesses of the network. It is the leveraging of operational and cyber experts that yield success.
Stuxnet is an example of this. Stuxnet is regarded as one of the most sophisticated, publically known cyber attacks to date and it sent a clear message that a company’s critical infrastructure is vulnerable to attacks. It demonstrated that what was once hypothetical is now reality. Stuxnet targeted an air-gapped infrastructure and rewrote PLC code aimed specifically at the Siemens system in the Iran nuclear facility – took advantage of seven vulnerabilities and spread throughout the network very quickly. Stuxnet showcased the capability of a nation state with the intent, operational understanding and resources to carry out such an attack.
What The Attacker Targets
For the oil and gas/pipeline companies, the product that is at the heart of their success doesn’t just reside in the pipelines that crisscross the U.S.; it also resides in the critical operational and business networks. The adversary wants access for information theft and position to carry out their agenda. Cyber criminals and nation states are looking for trade secrets: they desire the intellectual property that makes the GAS2U Company the GAS2U Company and enables it to successfully compete in the marketplace.
Just how bad is the ex-filtration (or criminal theft) of information from the U.S. to other nations? The commander of U.S. Cyber Command, Army Gen. Keith Alexander, said the ex-filtration of data from U.S. companies continues on a massive scale. Speaking at the Maneuvering in Cyberspace Conference in Linthicum, MD he said it is the “greatest raid on intellectual property” in history. He reported that one company had lost $1 billion in technology it had taken more than 20 years to develop. Also, in his testimony before the Senate Select Intelligence Committee on Feb. 1, 2012, FBI Director Robert Mueller said that cyber attacks “will eventually bypass terrorism as the biggest threat to U.S. security.” Some in the cybersecurity business argue (with supporting justification) that they already have, as attacks (Stuxnet and Shamoon) are increasing to test the ability to destroy critical infrastructure.
How Attacks Occur And Why It Is Challenging To Mitigate
There is a way to deliver 100% cybersecurity – construct a network, never turn it on, never let anyone use it and never connect it to anything. Some would call that a brick! To highlight how adversaries gain access and why it is difficult to deliver 100% cybersecurity, I will use some personal examples witnessed during U.S. military network vulnerability exercises and recent commercial vulnerability assessments.
The #1 tactic to access a network is through spearphishing (the engineering of an e-mail sent to users with a malicious payload – user clicks the link, payload is downloaded, malware spreads and access obtained). The often quoted industry averages of successful Spearphishing is 10% – but remember it only takes one successful attempt to compromise a network. It is important to note that companies who apply an “active spearphishing campaign” drive this percentage down to 3%.
Walking into an unoccupied office around lunchtime, I found a computer on, and the screen was not locked. I was able to pull up the person’s e-mail, stick a USB thumb drive into the computer, and launch software to capture information (to include password files). In another location, a recent install of network equipment had left certain network connections open, and the attack team was able to use this to our benefit. Another example was at a refinery: a wireless expert had shown up and identified open connections to the network that could have been exploited – these were quickly closed.
For companies the ability to determine an attack (or exfiltration of intellectual property) is challenging – and most are unaware that a network penetration has occurred. Or that they have ever been attacked – why? I offer a few comments to help understand the challenges all companies face:
• “A large-scale computer network (SCADA and PCS) is the most complicated thing humans have ever developed,” says Livermore engineer Jim Brase, who oversees several Laboratory efforts in cyber defense. Brase notes that commercial products such as antivirus software are useful at thwarting cyber attacks for stand-alone computers, however, they are inadequate for ensuring 100% defense of a large (hundreds) of network devices/computers from attacks orchestrated by well-resourced and determined cyber criminals.
• Finding the anomaly or “penetration point” is difficult – network experts can’t simply add “information odor” (like the rotten egg smell to natural gas) and locate the leak. There are large amounts of data flowing across and out of the company’s networks and the adversary works very hard to hide in plain sight! Unless the attacker wants you to know they are there – and then it is usually too late as the damage has been done. And the attacker has moved on.
• Attacks, especially those that exfiltrate intellectual property are designed to go undetected – only sophisticated monitoring and analytics tools can help detect and deter. Many companies have not made the right investment in the technologies or expertise to defend their networks.
Many companies believe they are not a target – nothing has gone wrong (yet) therefore, they don’t see the need to invest in the right expertise, technology or vulnerability assessment.
Given the complexity and scope of the networks, not to mention the numerous users, one can easily see how challenging it is to secure a company’s enterprise from the adversary. An energy company’s networks are large, complex and have numerous network devices, users and multiple access points. And the networks are constantly changing – expanding and being upgraded with new hardware and software.
And when you add the dynamics the adversary brings to the equation – no rules, time, nation state support, and the realization that they simply need to gain a single access point while cybersecurity experts protect a large enterprise – this task can seem daunting at best. However, once we understand the picture, we can begin to construct the puzzle’s borders – for the border establishes the boundary for our efforts and results.
Cybersecurity Risk Assessment – The Puzzle’s Border
The oil and gas/pipeline industry faces a constant barrage of cybersecurity threats that keep IT managers awake at night wondering if their networks are secure enough to deflect the next attack and how to convince the CFO to invest in the newest technology to improve their defenses. Too many organizations either suffer from 1) “regulatory adherence” in which they are meeting the intent of regulatory guidance (put in a firewall so we put in a firewall; execute the latest assessment checklist annually, so we comply) without fully determining if the solution delivers improved security while meeting the company’s operational priorities, or 2) attempt to apply a few “industry best practices” in the hopes that what worked for another GAS2U organization will work for them. Neither of these approaches is a rational strategy for determining risk and protecting information assets nor maximizing the value returned from investments in security.
Organizations must follow a coherent methodology for prioritizing and addressing cybersecurity risks – building The border that frames and helps guide all other puzzle actions. Risk can be determined by factoring the threat, multiplied by vulnerabilities and the consequences, to determine and assign risk values to specific operations and information. Resources are then aligned to those areas with the highest risk.
It sounds simple, but I have interviewed companies and performed vulnerability assessments where no Enterprise Cybersecurity Vulnerability Assessment or corresponding Information Security Strategy was produced. Without a strategy, companies are just fitting the “newest security solution piece” or “regulatory mandated guidance piece” into their overall puzzle actions – hoping it fits and will complete the picture. It is critical to ensure that the assessment focuses on all networks and interdependencies and looks at all aspects of cybersecurity (physical, user, policies, threat mitigation, redundancy/disaster recovery, information assurance, etc.), not simply the technology installed on the enterprise. Companies should use the results to document and implement a comprehensive risk-assessment strategy and align security investments with identified risks to deliver a “Defense in Depth” cybersecurity strategy and framework that matches operational priorities to security investments.
Protecting And Ensuring Operations – Group And Interlock The Pieces
Borrowing from best practices in solving complex jigsaw puzzles, a frequently used tactic is to group pieces into “like or similar” piles to better support the assembly of sections that ultimately will comprise the completed puzzle. For the oil and gas cybersecurity puzzle, I recommend the composition of upstream, midstream and downstream piles to better understand their unique complexities, vulnerabilities and interdependencies necessary to interlock and implement security solutions. A brief look at each of these is warranted to understand how they align to form a company’s cybersecurity puzzle piles; then comes the prioritization, integration, and adjustment of operational and cybersecurity actions (interlocking the pieces) to meet the ever-changing landscape and adversary threat vectors.
Upstream Operations The oil and gas industry makes significant investments to identify and manage their upstream assets around the world, and it is important to be sure that this valuable data will be safe from external threats or theft. It is therefore vital to keep your informational upstream assets competitive and secure in addition to keeping your physical upstream assets safe and operational. Cybersecurity breaches can compromise your valuable exploration data as the persistent and sophisticated threats will continuously attempt to mine your data through nontraditional and unsecured entry points.
You rely on timely notification of incidents to mitigate potential safety, environmental, and stakeholder issues as revenue stream depends on accurate reporting of resource production. At a conference, I was approached by the CEO of a large oil and gas company who told me they had a recent “knock on the door” and there stood an FBI agent who informed them that “a large nation state had penetrated their business and operational network” and was exfiltrating large amounts of information back to that country.
The company was unaware (normally the rule and not the exception), and after FBI forensic work, it was found to indeed be true. That penetration was “plugged”, the company is now smarter about the threat, the FBI moved on to the next company to stop the “information hemorrhage”, and the nation state moved on to other targets while continuing to locate and exploit vulnerabilities of the company from which their access was just removed.
Midstream Operations A company’s goal is the safe and continuous operation of midstream and pipeline operations, and the industry monitors pipeline operations in real time for delivery verification, measurement balance, leaks and other concerns. Your revenue stream depends on continuous operation and accurate reporting of pipeline operations, and an unintentional station shutdown has immediate effects on revenue and can potentially result in safety and environmental concerns.
Accurate reporting of these conditions is essential to incident response or maintaining production and it is important to assess your pipeline data management, control, and communication system for vulnerabilities and identify and neutralize threats. Long pipeline systems cannot be contained in a fenced area and must use other means to ensure protection. In recent publications, there have been discussions that the industry is looking to expand its reliance on remote control applications to safely shut down and respond to emergencies. Remote monitoring for physical site access alarms can be compromised, and a cybersecurity attack on these operations can occur without warning. A company is relying on SCADA systems to control operations, and it is important to evaluate your midstream operations for cybersecurity vulnerabilities and help close the gaps to protect your assets. As remote sensing increases, companies must be aware of the growth in wireless connections to their enterprise and take into account the vulnerabilities that are introduced – wireless and mobile devices will continue to benefit both the industry and the cyber hacker.
Downstream Operations Refinery, petrochemical, and specialty chemicals manufacturing operations must be reliable and controllable. While most companies have made vast improvements to the “fence-line” protection of their plants and physical infrastructure, recent attacks against control systems have made security a high priority in the protection of downstream facilities. The operational expert and “well-resourced” hacker are very aware that these systems are integral to the operations and performance of all major refineries and petrochemical plants as well as the pipeline transmission systems. The downstream oil and gas sector operates within a highly diverse and often decentralized infrastructure.
The SCADA and Process Control Systems (PCSs) used today by refineries, petrochemical plants, and pipeline operations are the primary means of controlling most oil and gas processing and distribution in the United States and around the world. In order to supply corporate decision makers with real-time critical data, companies have integrated these SCADA and PCS systems with corporate business systems, thereby creating the potential for unauthorized access to critical process control systems through their corporate networks.
Some in the industry have the misconception that SCADA technology is too specialized for “hackers” to take advantage of, or that attempting to limit the availability of such information is an effective deterrent. This is not true – but the cyber hacker would like companies to continue thinking it is. The recent attacks on Iran via the Stuxnet engineered attack and other energy companies’ networks show that a company’s security strategy must take into account the Business, Process Control and SCADA networks.
Puzzle “Experts” – Seek Experience
There are numerous “experts” and ongoing activities to assist an oil and gas/pipeline industry in solving their cybersecurity Puzzle. Some examples are:
• The National Institute of Standards and Technology (NIST) has published the Guide to Industrial Control Systems Security (800-82).
• The North American Electric Reliability Corporation (NERC)has published the Reliability Standards for Critical Infrastructure Protect.
• DHS and DOE are working to provide support – the latter producing the Capability Cybersecurity Maturity Model and the Cybersecurity Risk Management Process Guideline.
• Idaho National Lab has training on SCADA security and supporting research; Sandia is also working in cybersecurity.
• Nationally recognized institutions such as INGAA, SGA and API are promoting events to bring Operational and Cybersecurity experts together to define the challenges and seek solutions; INGAA has recently established a Cyber Committee to advance recommendations for the oil and gas/pipeline industry.
• Universities such as Rice, Virginia Tech, Georgia Tech Research Institute, and the University of Oklahoma at Tulsa are examples of academia working on critical infrastructure security areas
• And finally, industry partners, like URS and others who are taking their DoD and U.S. government cybersecurity experience, integrating it with their oil and gas operational acumen and presenting military-grade cybersecurity “puzzle-solution” to the industry.
In conclusion, I offer the following “Puzzle Cliff Notes” to help oil and gas pipeline companies succeed in solving their specific cybersecurity puzzles:
• Perform an enterprise cybersecurity vulnerability assessment. Develop and implement a comprehensive risk-assessment strategy and align security investments with identified risks.
• Understand your organization’s information, who wants it, and what tactics adversaries might use to get it. Remember, it is about protecting against ex-filtration and manipulation of data, followed by enterprise resilience, and preventing disruption, degradation and destruction attacks.
• Leverage “Proven” Cybersecurity expertise and solutions to build a Defense in Depth posture for Cybersecurity
• Exercise and validate your cybersecurity strategy – it is not a matter of IF you will be attacked, but WHEN and how successful the attack will be.
Finally, we should always remember that there [likely] is [at least one] nation state using experts in the oil and gas/pipeline industry and cyber espionage to develop a ways to disrupt your operations, degrade your marketplace performance or destroy your capability to execute your business or worse – cause an environmental or safety mishap. It is imperative that we bring together a team of experts to solve our cybersecurity puzzle and defend against attacks.
The Author
Dean G. Fox serves as Vice President, Cyber Strategy for the Federal Services division of URS where he spearheads strategy development for the identification, development, delivery and program management of Cybersecurity and Information Technology (IT) programs across the Department of Defense (DoD), Homeland Security, Federal and Private Sector. He is responsible for engaging his team’s D “military grade” cybersecurity expertise and experience to deliver solutions and Cyber consulting that focus on securing URS’ diverse private sector Energy clients operations and information enterprise ( i.e., critical infrastructure, pipelines, refineries, power plants, power generation and nuclear). Dean served 28 years in the U.S. Air Force, retiring as a colonel. He served as Director of Communications and Information (Chief Information Officer) for 13th Air Force in Hawaii and was responsible for all communications and cyber activities in the Asia-Pacific region. Dean was also the Deputy Director of Communications and Information at Headquarters, US Pacific Command (USPACOM), expanding his cybersecurity, IT and communications responsibilities throughout the entire Asia-Pacific region while personally engaging over 28 nations and respective senior leadership.





Comments