February 2012, Vol. 239 No. 2
Features
Next Generation Cyber Attacks Target Oil And Gas SCADA
Anyone working with SCADA or industrial control systems (ICS) in the oil and gas industry is aware of the pressure to increase productivity and reduce costs through network integration. For example, sharing real-time data from field operations with management is standard practice for most companies. Similarly, the demand for remote support has made many pipeline control systems accessible via Internet-based technologies.
At the same time, SCADA systems themselves have changed radically. Proprietary networks have been replaced with equipment using Ethernet technology. Single-purpose operator stations have been replaced with computers running Windows™, and IT software such as PDF readers and web browsers are installed in every station or control center.
These new technologies are enabling companies to implement agile, cost-effective business practices. Unfortunately, they also come at a cost – many of the same security vulnerabilities that have plagued business systems now appear in SCADA systems. Pipeline control systems are now exposed to cyber-security threats they were never designed for.
Stuxnet – The Game Changer
Cyber attacks on automation systems were considered by many to be a theoretical problem until the discovery of the Stuxnet worm in July 2010. At that moment the world changed, not only for oil and gas companies, but also for automation vendors, hackers, criminals and even governments.
Stuxnet was specifically designed to attack Siemens automation products. It was capable of downloading proprietary process information, making changes to logic in PLCs, and then covering its tracks. It employed previously unknown vulnerabilities to spread. It was powerful enough to evade state-of-the-art security technologies.
Stuxnet’s intended target was the uranium enrichment centrifuges used by Iran in its nuclear armaments program. Seizing control of the automation system, the worm was able to reconfigure the centrifuge drive controllers, causing the equipment to slowly destroy itself.
Stuxnet had a specific target, but like all attacks, cyber or conventional, there was collateral damage. Several companies in the U.S. had PLCs that were reconfigured by Stuxnet, probably by accident. No real damage, but a lot of labor charges were incurred and shutdowns occurred.
Even these problems soon stopped; software patches and anti-virus signatures soon drove Stuxnet into extinction. Unfortunately, the problem did not end there.
Stuxnet’s Children Have Arrived
The real impact of Stuxnet began to appear after the worm itself was history. Thanks to Stuxnet’s publicity, hackers and criminals discovered that SCADA/ICS products are attractive targets. These systems soon became targets of choice for public security disclosures; in 2011 the U.S. ICS-CERT released 104 security advisories for SCADA/ICS products from 39 different vendors. Prior to Stuxnet, only five SCADA vulnerabilities had ever been reported.
What was particularly concerning is that attack code was released for 40% of these vulnerabilities. This meant that the bad guys both knew where to find holes in SCADA/ICS products and had the software to exploit them.
Stuxnet also showed the world the power of a well-designed ICS worm. It could steal corporate secrets, destroy equipment and shut down critical systems. And while Stuxnet appeared to have been created for political reasons, the opportunities for corporate exploitation were obvious to governments and criminals alike. It was only a matter of time before someone re-used the techniques from Stuxnet to go after other victims.
By February 2011, a new attack against industry was exposed. A paper titled “Global Energy Cyberattacks: Night Dragon,” described cyber-threat activity that was stealing sensitive data such as oil field bids and SCADA operations data from energy and petrochemical companies.
In early October 2011, a variety of sources announced the discovery of a new trojan named “Duqu”. This targeted malware used a lot of the same source code as Stuxnet. Unlike Stuxnet, it is an information stealer and doesn’t appear to directly target PLC systems. However, according to Symantec: “Duqu’s purpose is to gather intelligence data and assets from entities such as industrial infrastructure and system manufacturers… The attackers are looking for information such as design documents that could help them mount a future attack on various industries, including industrial control system facilities.”
At the end of October, Symantec released details of a third attack directed at 25 companies involved in the manufacture of chemicals and advanced materials. Calling these attacks the “Nitro Attacks,” Symantec reported: “The purpose of the attacks appears to be industrial espionage, collecting intellectual property for competitive advantage.”
Why Do They Do It?
When most people consider the motivation of worm creators and hackers, they think of the destructive focus of early cyber events like the Slammer worm in 2003. That worm shut down vast portions of the Internet and affected companies around the world.
Today’s new attacks show a different focus, characterized by subtle and persistent attempts to steal valuable information – information that can be used to make a counterfeit product, out-bid a rival for an oil exploration lease, or coordinate a short selling campaign against a company’s stock.
Theft of operations information for commercial espionage has been around long before networks and cyber security showed up. Check out the article “The Pizza Plot” for an example of how production data from a Kraft food plant was used by a competitor to reshape the $2.3 billion pizza market. Today the profit potential for SCADA information theft can be even bigger.
These worms could also be precursors to later destructive attacks against automation systems. Clearly, the Stuxnet designers collected detailed process information on their victim prior to actually creating their worm. Could the Duqu worm be a forerunner to a more destructive attack?

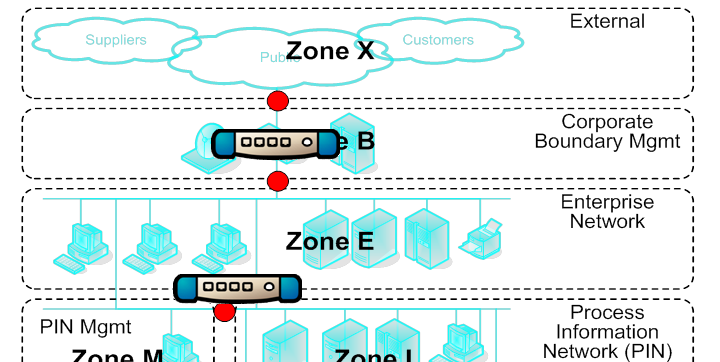
Figure 1: Zone and Conduit Strategy Secures Refinery.
It is worth noting that the goal of Stuxnet was to impact Iran’s production rather than harm people. So it is possible that the goal of this next generation of malware is to quietly stop business processes at a utility or pipeline somewhere in the world. Impacting the production of a rival, short-selling the shares of a company or extorting money under the threat of a disruption are all profitable activities for a criminal or nation-state group.
Can’t Keep It Out
Here is why we can’t keep Son-of-Stuxnet out of our systems. Many security experts suggest the only solution is to go back to the days of completely isolated automation systems. Unfortunately, walling off a control system just isn’t feasible today. As I explained in the article “#1 ICS and SCADA Security Myth: Protection by Air Gap,” modern industry depends on a steady diet of electronic information from the outside world to operate. Cut off one source of data into the SCADA system and another (potentially riskier) “sneaker-net” source replaces it.
Industry and government can try to battle this trend by banning technologies and mandating procedures. We see this sort of strategy every time we try to board a plane and wait in long lines to take our shoes off. Frankly, I don’t think it is effective security for air travel. It is even worse for companies that need to be profitable if they are going to stay in business.
The Way Forward
Is the situation hopeless? No, but security practices must improve significantly. First, industry needs to accept the idea that complete prevention of SCADA system infection is impossible. The article, Cyber Security And The Pipeline Control System (Feb. 2009), showed that determined attackers have many pathways available to them, not just the obvious ones like Internet connections. As a result, no matter what we do, some SCADA assets will suffer compromise over the life of a system.
The only solution is to do what the human body does to defend against nasty viruses. It can’t keep them all out (you do have to breath), so it has excellent systems for the rapid detection of a hostile entity. It does not just monitor what passes through your mouth – it monitors your entire body. Once something bad is detected, the immune system immediately goes to work to isolate and control it. Similarly, for effective SCADA security, pipeline operators need to:
1) Consider all possible infection pathways and have strategies for managing each one. Don’t just focus on the obvious like the corporate firewall or USB thumb drives.
2) Aggressively sub-divide ICS networks to limit the consequences of a compromise. The ANSI/ISA99 and IEC-62443 standards call this building a zone-based defense.
3) Define choke-points (called conduits in the ANSI/ISA and IEC standards) between zones, where you can control or even shut off network traffic in cases of emergency. Figure 1 shows a zone and conduit model deployed in a large North American refinery.
4) Look beyond traditional IT firewalls for your SCADA zone controls, toward firewalls capable of deep packet inspection of industrial protocols. This is important because worms like Stuxnet have shown how easy it is to piggy-back on valid traffic to escape detection.
5) Focus first on securing mission critical systems, particularly safety integrated systems (SIS).
6) Include security assessments as part of the periodic maintenance processes.
7) Work to improve the culture of security among management and technical teams.
Implementing these changes will improve the “defense-in-depth” posture for any pipeline ICS/SCADA system and help protect your operation from cyber espionage. Better SCADA security is needed urgently; waiting for the next worm may be too late.
(end)
Author
Eric Byres, P. Eng., ISA Fellow, is chief technology officer and vice president, Engineering, for Tofino Security Product Group, Belden Inc. Contact information: info@byressecurity.com. Added contact information: Heather MacKenzie, heather.mackenzie@tofinosecurity.com, 250-390-1333.
References And Further Reading
#1 ICS and SCADA Security Myth: Protection by Air Gap:
http://www.tofinosecurity.com/blog/1-ics-and-scada-security-myth-protection-air-gap
Stuxnet Central:
http://www.tofinosecurity.com/stuxnet-central
U.S. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT):
https://www.us-cert.gov/control_systems/ics-cert/
Global energy Cyber Attacks “Night Dragon”:
https://www.mcafee.com/us/resources/white-papers/wp-global-energy-cyberattacks-night-dragon.pdf
W32.Duqu – The precursor to the next Stuxnet:
http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w32_duqu_the_precursor_to_the_next_stuxnet_research.pdf
The Nitro Attacks – Stealing Secrets from the Chemical Industry:
http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/the_nitro_attacks.pdf
The Slammer Worm:
http://en.wikipedia.org/wiki/SQL_Slammer
The Pizza Plot:
http://www.tofinosecurity.com/sites/default/files/Pizza%20Plot.pdf





Comments